Environment: Debian 9 sid
Updated: add basic gcc c compiler on fresh install env
DNSCrypt server installation
$ apt install libevent-dev autoconf make libsodium-dev build-essential
$ git clone git://github.com/cofyc/dnscrypt-wrapper.git
$ cd dnscrypt-wrapper
$ make configure
$ ./configure
$ make installGenerate SSL, Public key, Private key, Cert
$ mkdir ~/dnscrypt-key
$ cd dnscrypt-key/
$ dnscrypt-wrapper --gen-provider-keypair \
--provider-name=2.dnscrypt-cert.<yourdomain> --ext-address=<external server ip> --dnssec --nolog
* If your server doesn't store logs, add --nolog and if it supports DNSSEC, add --dnssec.
This will create two files in the current directory: public.key and secret.key.
// Generate SSL
$ dnscrypt-wrapper --gen-crypt-keypair --crypt-secretkey-file=./ssl.key
// Generate Cert
$ dnscrypt-wrapper --gen-cert-file --crypt-secretkey-file=./ssl.key --provider-publickey-file=./public.key --provider-secretkey-file=./secret.key --cert-file-expire-days=365 --provider-cert-file=ssl.certIf you forgot your public key, run this command
$ dnscrypt-wrapper --show-provider-publickey --provider-publickey-file ./public.keyAdd generated TXT into your DNS Record
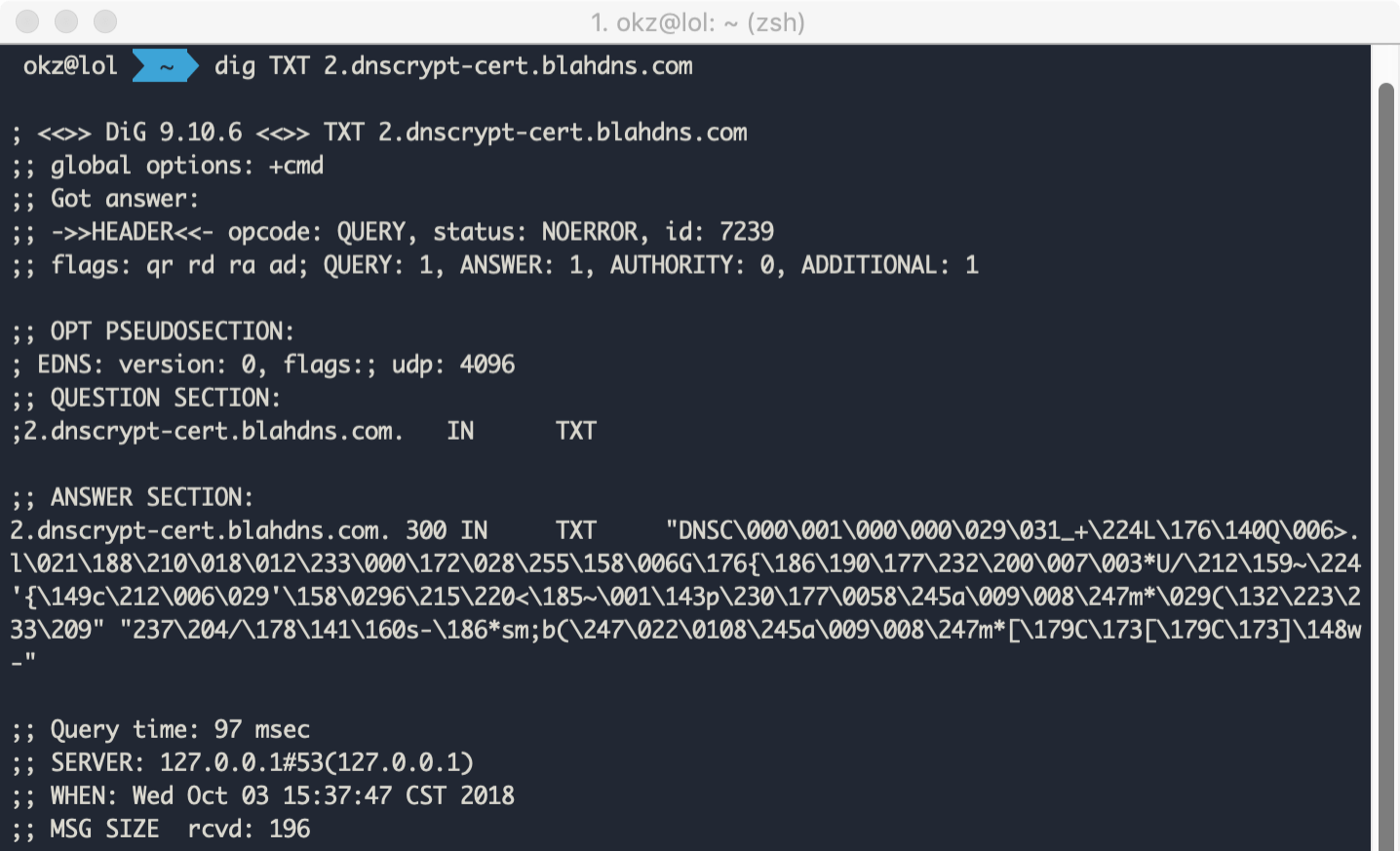
If you forgot the TXT, you can get again with this cmd
$ dnscrypt-wrapper -r --crypt-secretkey-file=ssl.key --provider-cert-file=ssl.cert --show-provider-publickey-dns-recordsStart the server
Before you start your server, please make sure you already have those files in your
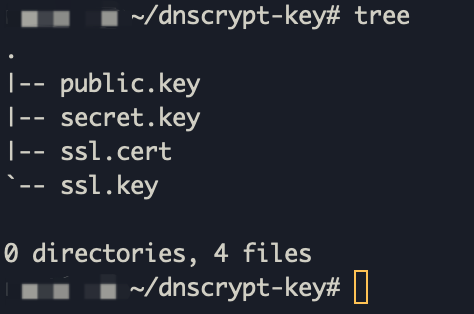
// IPv4
$ dnscrypt-wrapper -d -r 127.0.0.1:53 -a 0.0.0.0:8443 --crypt-secretkey-file=ssl.key --provider-cert-file=ssl.cert --provider-name=2.dnscrypt-cert.blahdns.com -VVV
// IPv6
$ dnscrypt-wrapper -d -r 127.0.0.1:53 -a [::]:8443 --crypt-secretkey-file=ssl.key --provider-cert-file=ssl.cert --provider-name=2.dnscrypt-cert.blahdns.com -VVVReferences:
1. https://github.com/cofyc/dnscrypt-wrapper
2. https://03k.org/dnscrypt-wrapper-usage.html
Featured Photo by John Carlisle on Unsplash
